Our Cybersecurity Solutions
A Layered Security Approach
Managing network security can be complicated, but ensuring that your network is secure from malicious threats shouldn’t be.
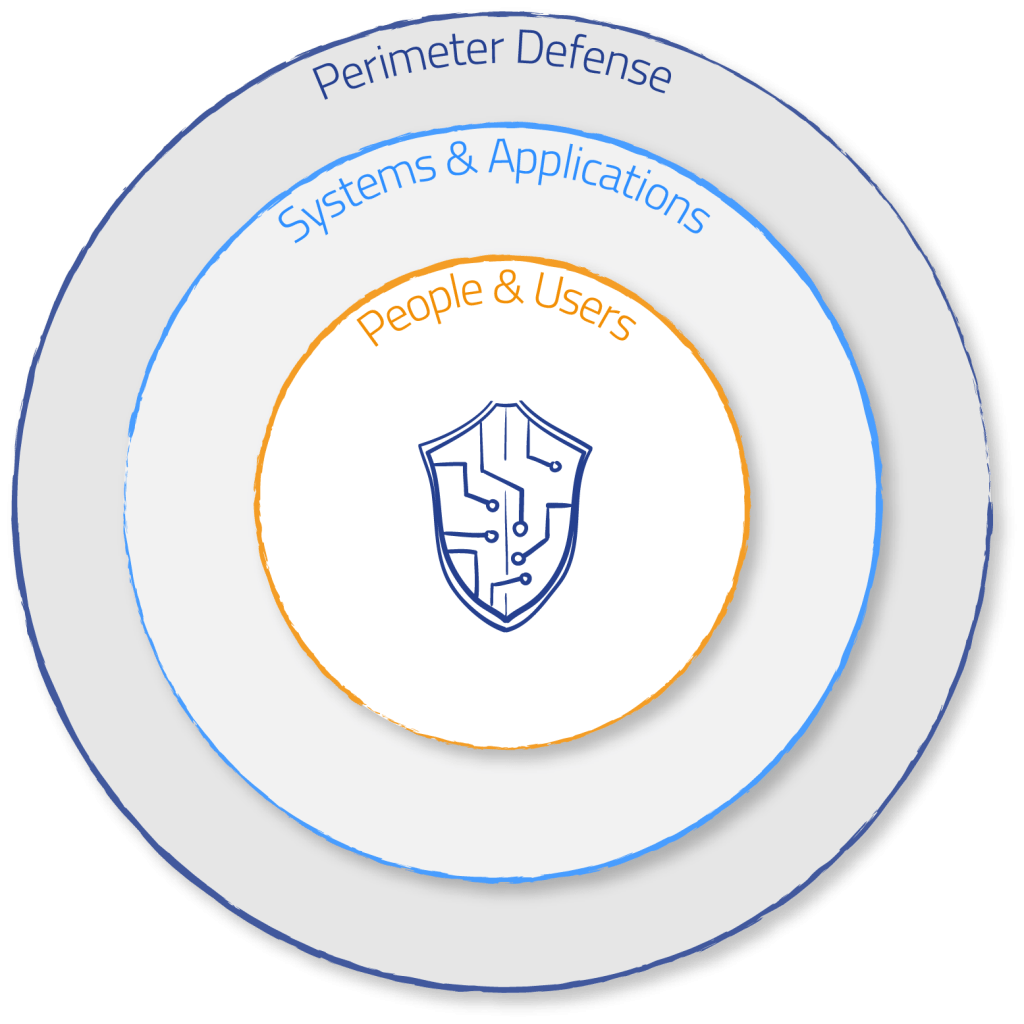
Perimeter Defense
IT security threats are rapidly evolving. With advanced artificial intelligence, compromises to the health of IT and operations come in a variety of forms to safeguard a perimeter around your company’s data.
Key Elements Include:
- Firewall with deep-inspection capability
- URL Content Filtering
- Penetration Testing
Systems & Applications
Your network needs constant maintenance to stay secure. This means patching vulnerabilities and actively managing patches, as well as implementing intelligent spam filters and AI-powered anti-virus and anti-malware programs.
Key Elements Include:
-
Intelligent Spam Filtering
-
Vulnerability Patching
-
Patch Management
-
Antivirus & Anti-malware
People & Users
Over 60% of all data breaches in organizations originate from unauthorized access from a third-party vendor, a former employee or a current one. The majority of breaches that occur today are the result of an unsuspecting employee clicking something they should not have.
Key Elements Include:
- Awareness Training
- Safe Social Media Practices
- Business Email Compromise Training
What are your risks?
A security assessment is the cornerstone of any IT security strategy.
What We Do
Multi-Factor Authentication
MFA is often ignored because speed is given more weight than security by employees, but MFA is also more functional at safeguarding data than any other single security measure. Implementing this across systems will do more for your security than almost any other single measure.
Security Awareness Training
According to the FBI, business email compromise is the number one threat for businesses in the US. We offer in-depth and easy-to-adopt security awareness training to uncover flaws in security and keep your staff up to date.
End Point Detection & Response
End-point detection is the next generation of anti-virus and anti-malware. We provide, install, and manage next-generation endpoint protection leveraging best-in-breed software. The architecture allows us to stop never-before-seen threats before other platforms can detect them.
Data Backup & Recovery
Restoring data can take a substantial amount of time and money, and that’s if the data can be recovered at all. We give you speed, convenience, and reliability with our automated backup system, which reduce recovery time objectives (RTOs) and recovery point objectives (RPOs).
Take the First Step to Better IT: Contact Us Today!
To learn more, contact us today at (828) 274-1196.

















